Autonomous reliability meets maximum security
Causely's architecture keeps you in control of your data, letting you proactively eliminate risks without compromising compliance.


How we protect
your data
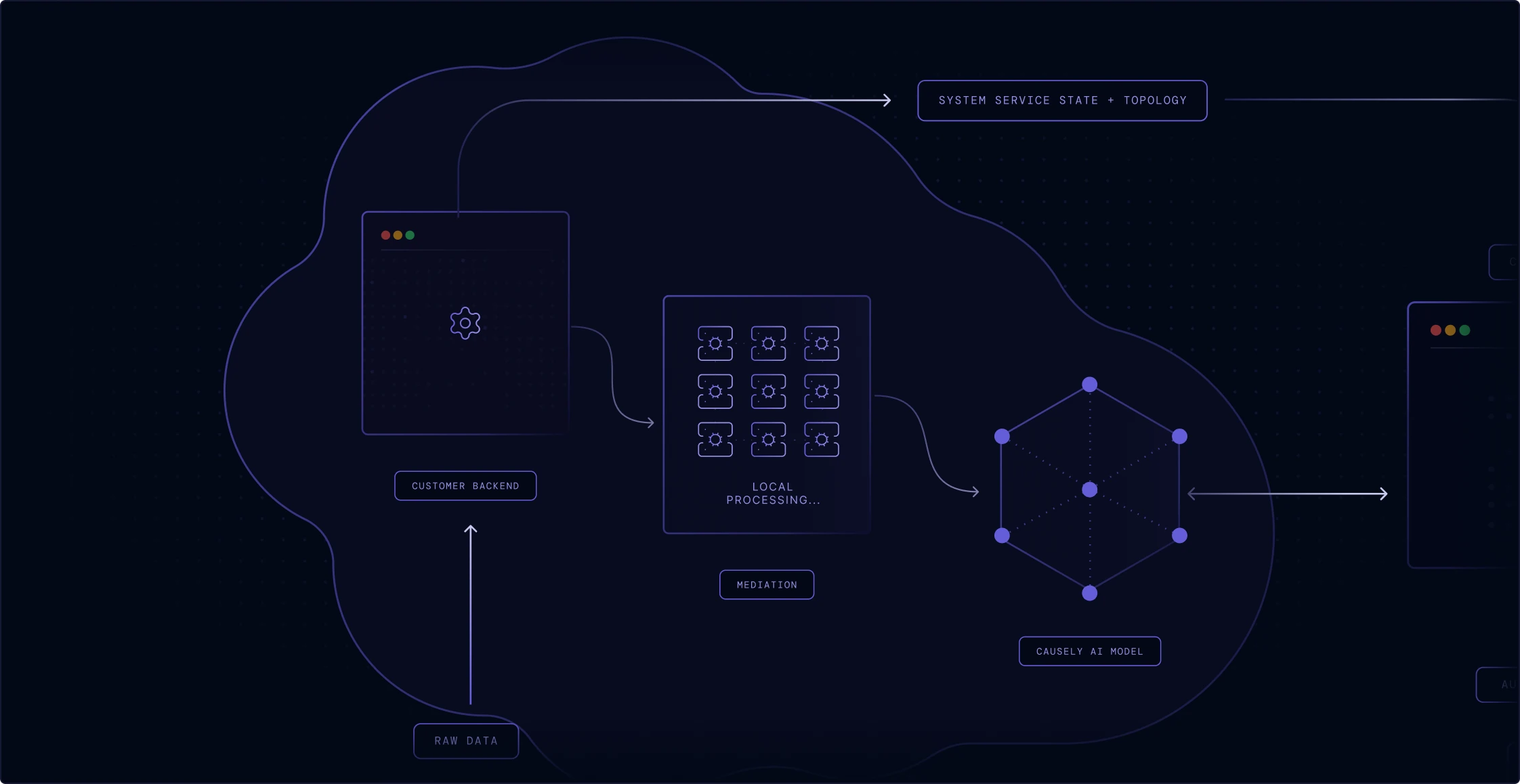
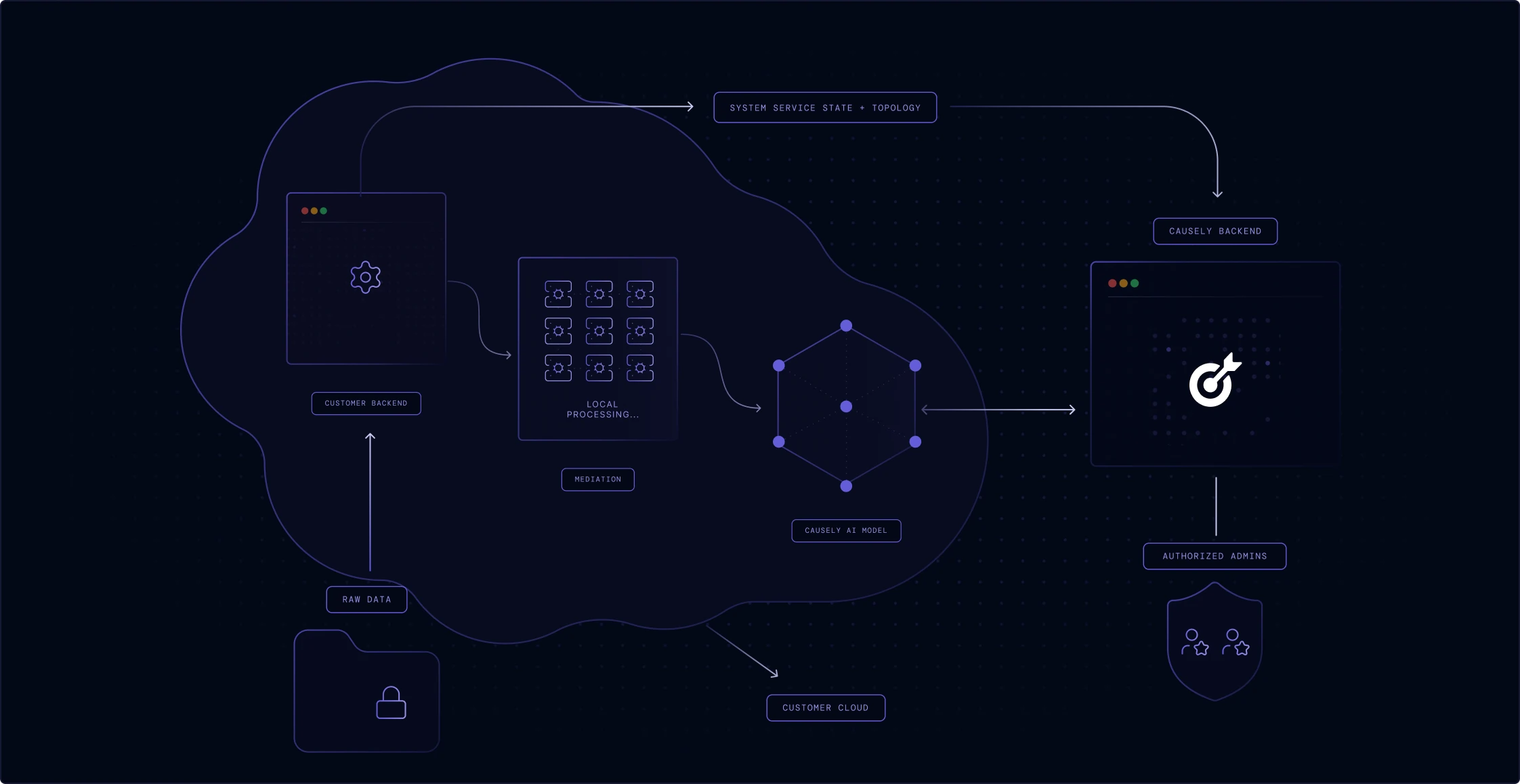
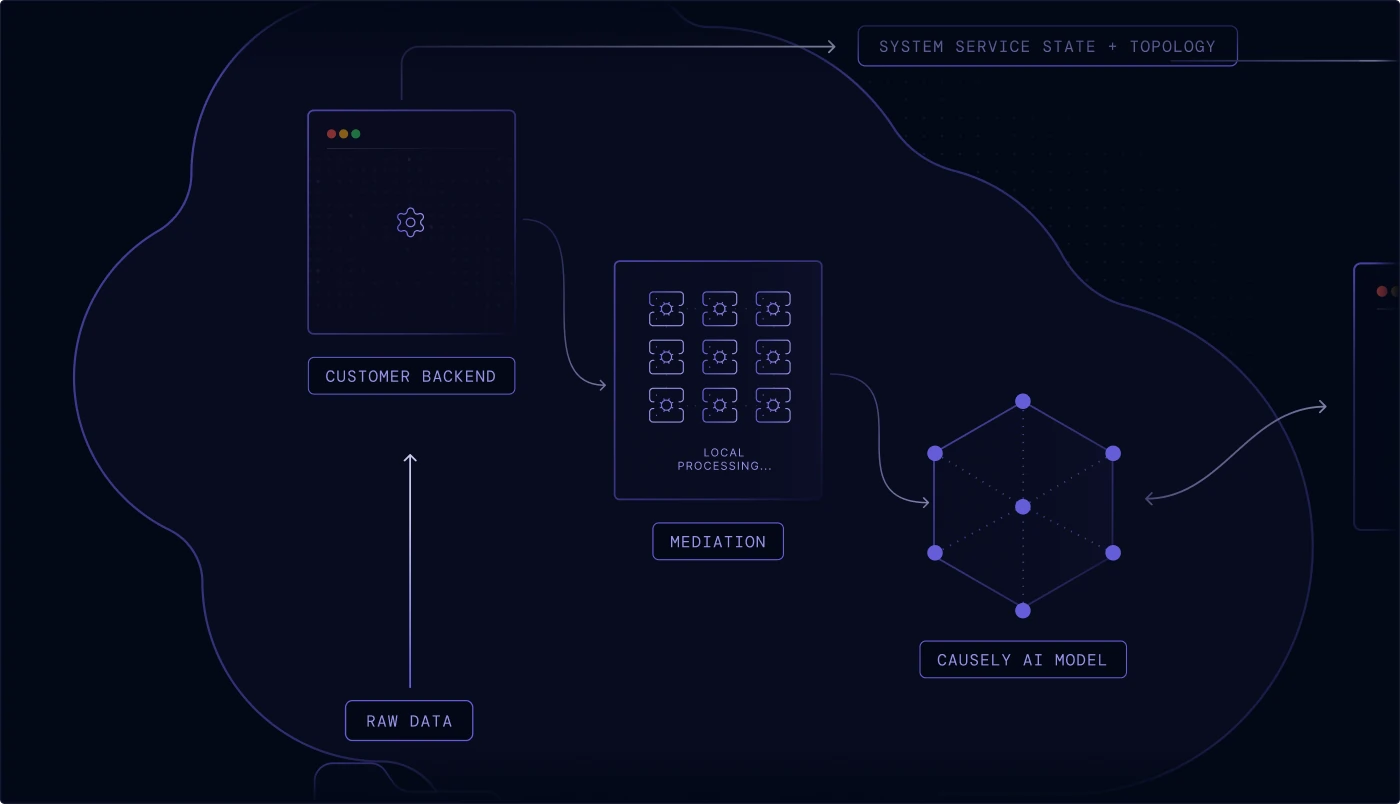
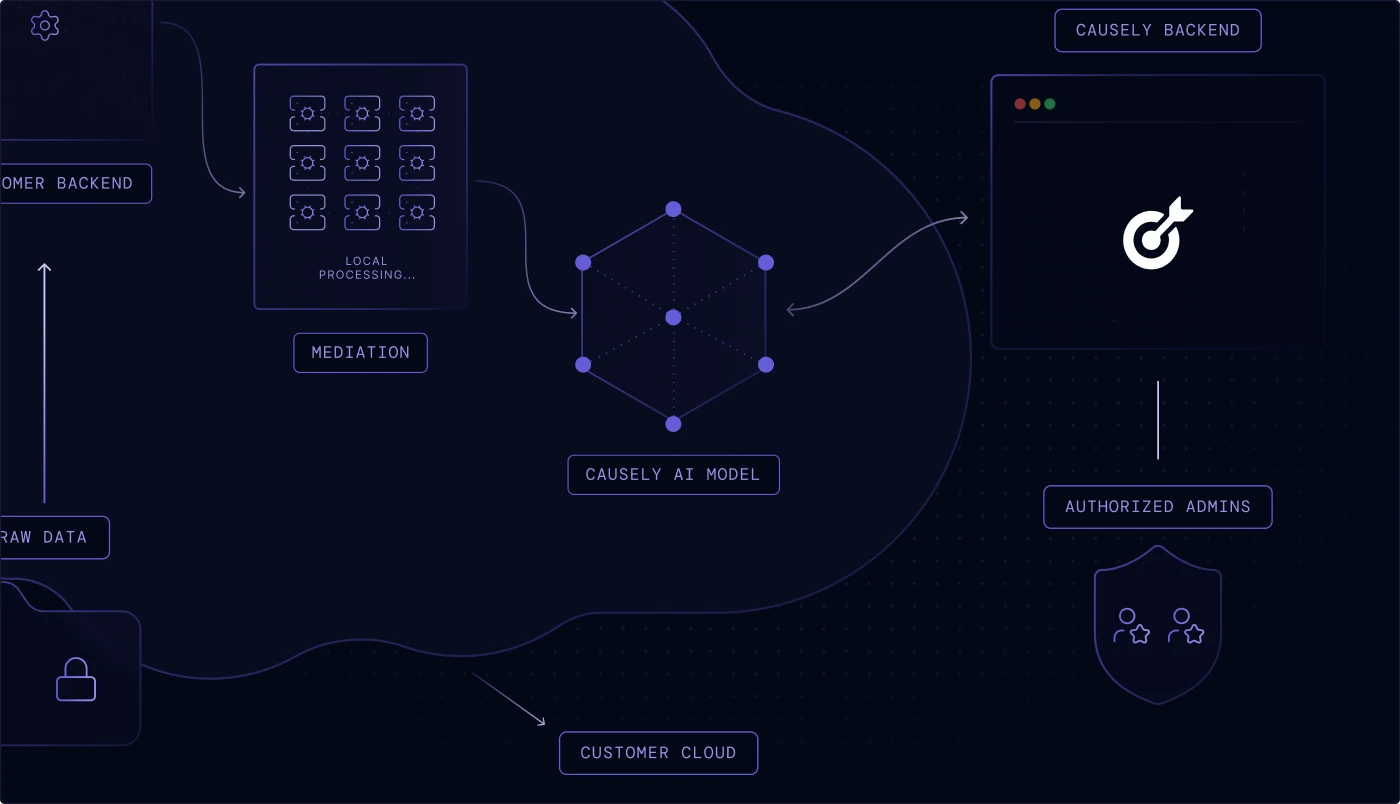
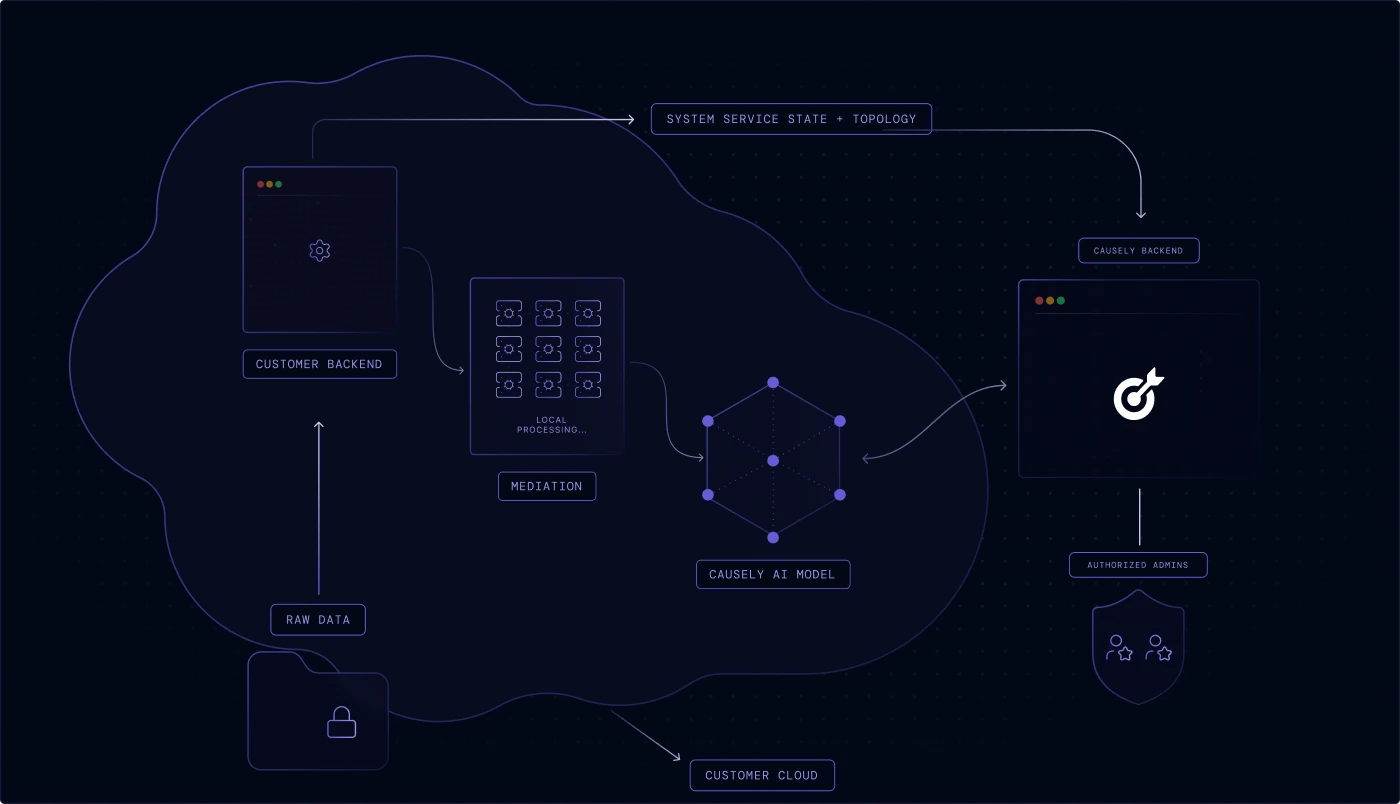
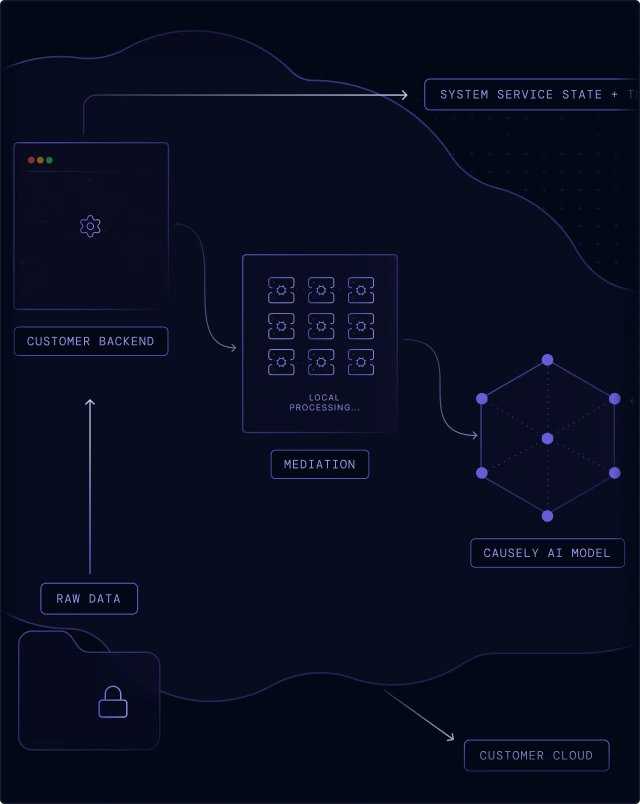
Causely is architected to keep your most sensitive information local, ensuring you maintain control and sovereignty over your telemetry.
Data minimization
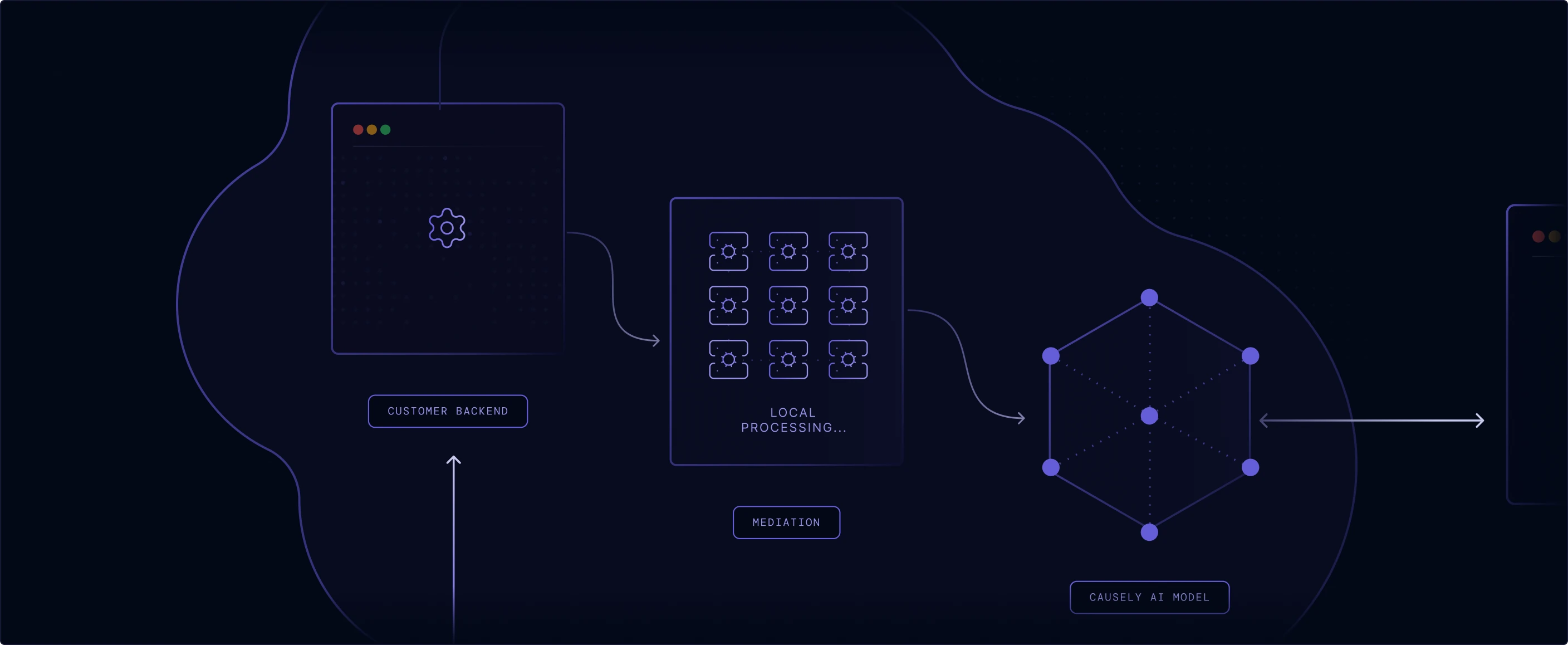
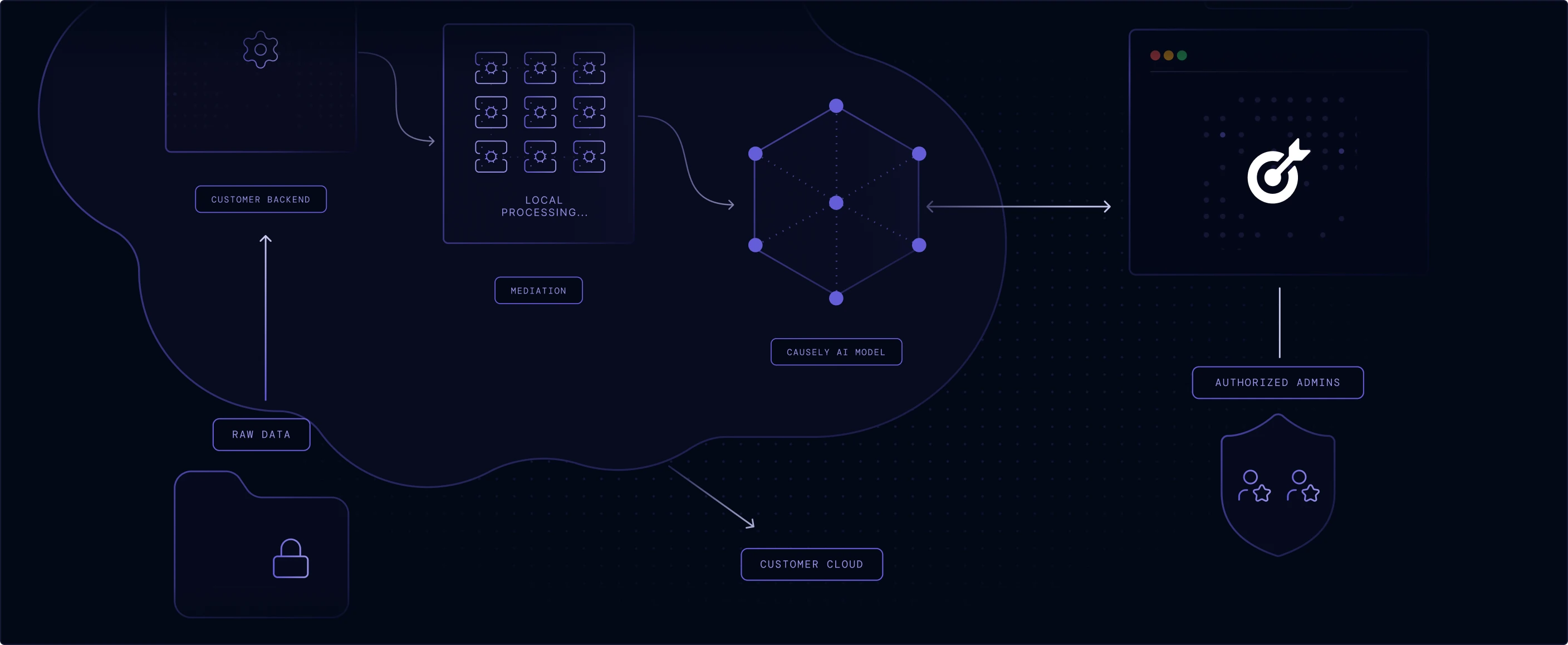
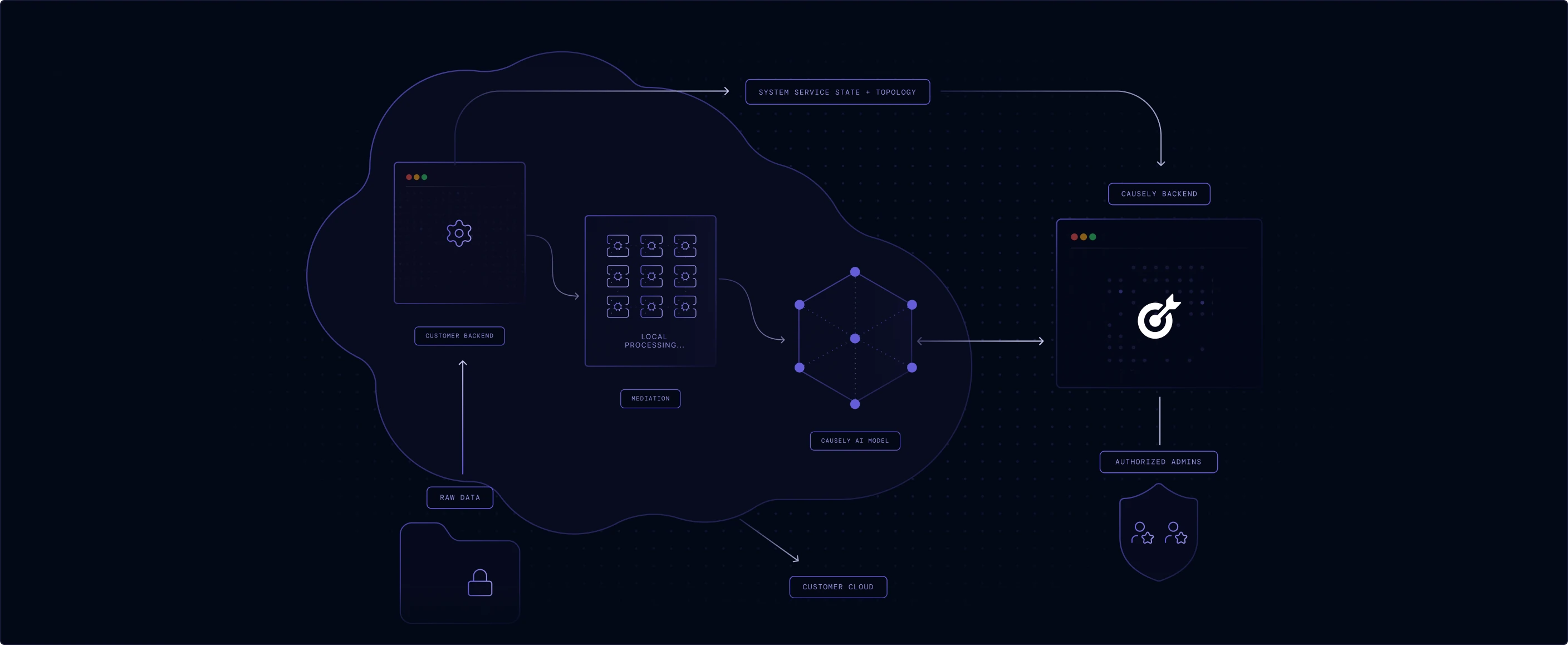
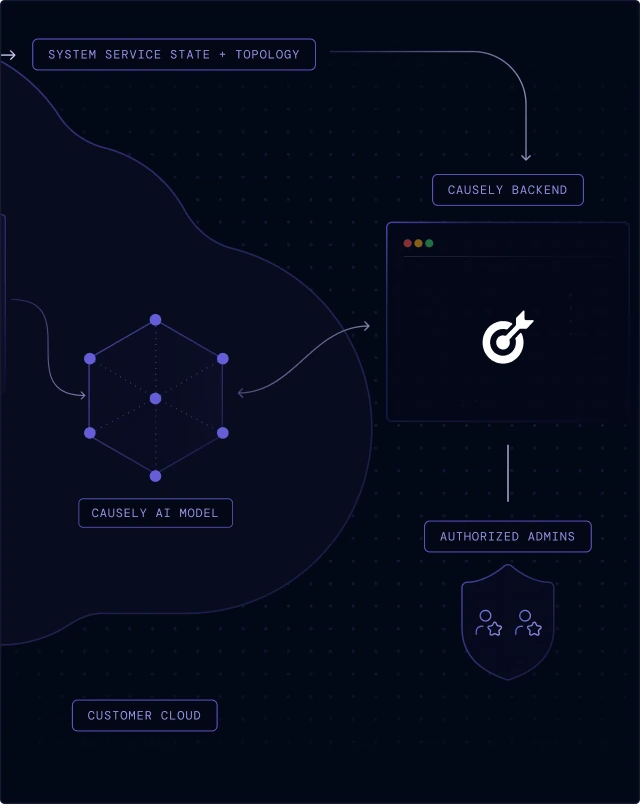
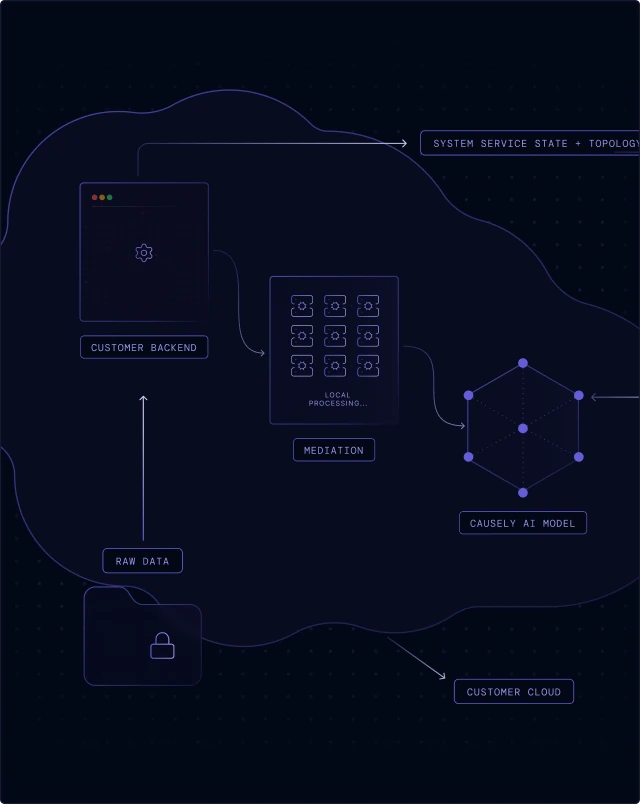
Raw source data is retained in your environment and never transmitted to the SaaS backend—we only send distilled symptom state and service topology.
No sensitive data storage
No sensitive data or Personally Identifiable Information (PII) is stored or processed. All symptom data transferred is encrypted both in transit and at rest.
SOC 2 Compliance
Causely adheres to strict security standards, giving your team the confidence that our platform meets the rigorous demands of enterprise compliance.
Designed for complete
privacy and control
Causely runs on a flexible, hybrid architecture that separates data processing from causal intelligence, offering unparalleled deployment control and minimal exposure.
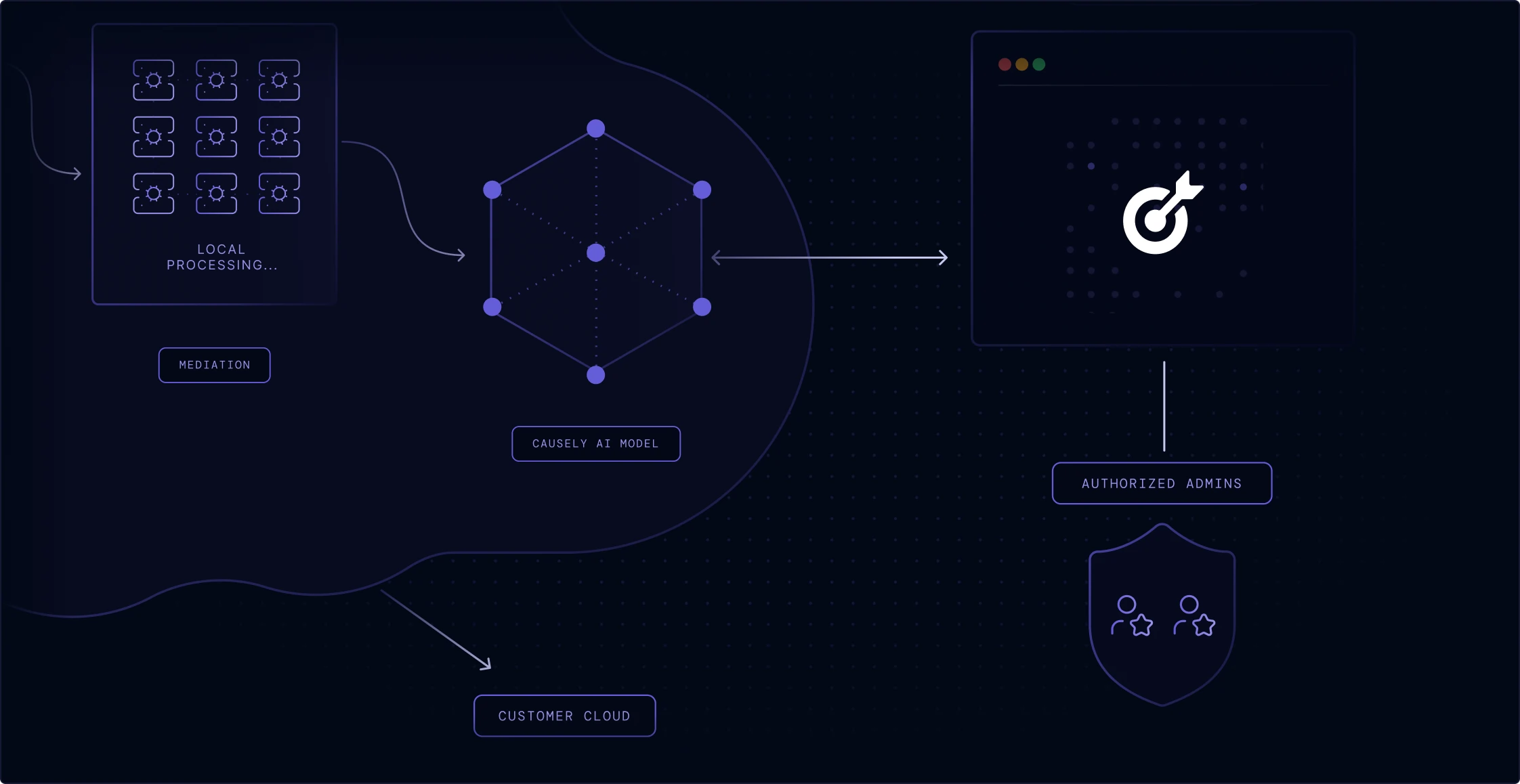
Local Mediation
The mediation layer performs all local processing and symptom detection. It operates with minimal privileges and never accesses sensitive information.
Access Control
Access to the Causely SaaS infrastructure is strictly restricted to a select group of authorized personnel responsible for operating the service.
Bring your own cloud option
Run the entire application within your own environment, keeping all data and processing behind your network boundary for increased security or airgap deployments.
Operational security
and AI agents
We prioritize security through robust deployment controls and full transparency regarding the operational needs of our platform components.
Granular privilege control
Specialized components like the eBPF Agents, which require elevated access for deep kernel visibility, can be controlled or disabled during deployment.
Agent isolation
Agents do not establish outbound connections to the internet or any services other than the mediator, ensuring a tight security perimeter around data collection.
Security across the stack
Security controls are consistently applied across cloud platforms (AWS, GCP, Azure) and on-prem deployments, providing a consistent, secure foundation.
Read the full report
We are committed to full transparency regarding our security practices. If you’d like to read more about our approach to security and compliance, take a look at our SOC 2 report.